We effortlessly scale and configure decentralised identity
Elevate your Identity Verification with Cenda.
Unlock the power of decentralised identity with Cenda, Condatis’ innovative solution that with market leading, Microsoft Entra Verified ID takes organisations to the next level of digital identity.
Built to put users in control of their data using verifiable credentials, decentralised identity replaces data held within siloed databases with self-owned credentials.
| Using cryptographic techniques, decentralised identity ensures integrity and security. | Streamline identity processes to save time, resources and costs by eliminating third-party identity verification services. | Significantly reduce the risk of cyber attacks by removing central authorities or intermediaries. |
With Microsoft Entra Verified ID employees, customers and partners have a portable digital identity that tackles the modern identity verification challenges faced today and facilitates zero-trust decision making. Organisations can enhance flexibility for their users by providing seamless and secure access to apps and resources using their identity credentials.
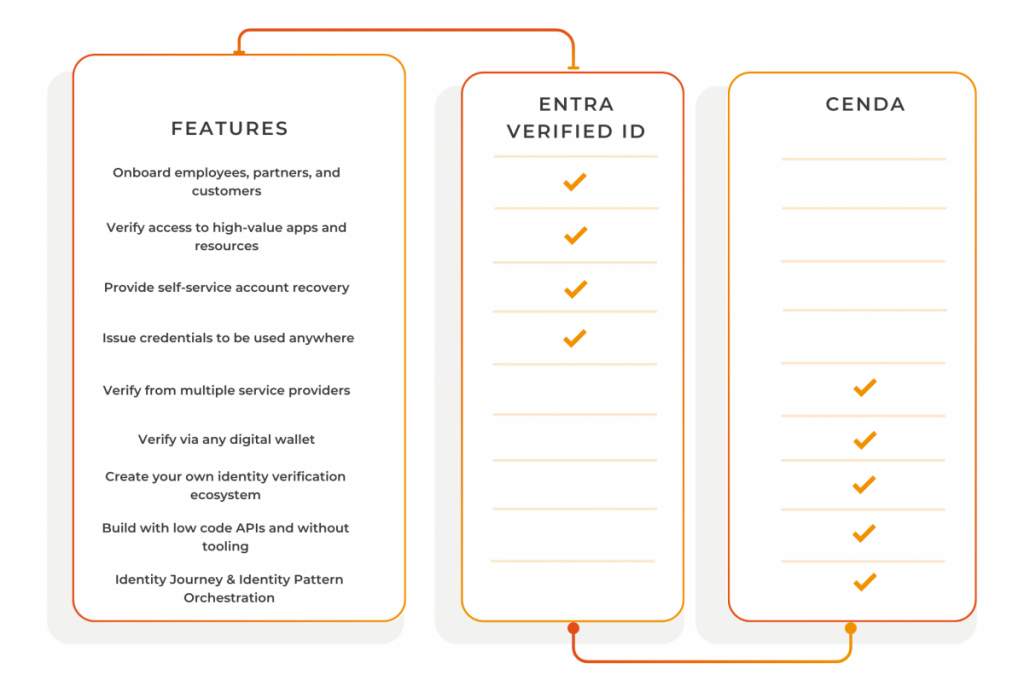
Our team of experts have meticulously created a product that enables disparate systems and frameworks to interoperate with our recommended decentralised identity solution, Entra Verified ID. As a curated set of technologies and tools within a decentralised identity engineering platform, Cenda empowers organisations to seamlessly implement solutions with diverse service providers, digital wallets and trust frameworks and use the Microsoft Entra ecosystem as their identity backbone. Verifiable credentials represent the future of digital identity, employing cryptographic techniques to minimise costs, maximise security, and streamline user onboarding. Entra Verified ID facilitates credential issuance and verification but implementation scenarios can become complex and a critical challenge to decentralised identity adoption will be system, standard, and framework interoperability. Cenda addresses this by solving key risks associated with scenarios where: With the Cenda, organisations can effortlessly scale and configure their Entra Verified ID solution, ensuring a seamless experience in any situation, now, and in the future.How does Cenda fit in?
Why choose Cenda?
We are a trusted Microsoft implementation partner for accelerating decentralised identity adoption of Microsoft Entra Verified ID. Our specialisation across Microsoft Entra identity and access products, paired with our Driving innovation with Microsoft, our trusted identity partner
 experience in deploying decentralised identity solutions at scale, makes Condatis a safe pair of hands to help you navigate the complexities that arise when handling large data siloes.
experience in deploying decentralised identity solutions at scale, makes Condatis a safe pair of hands to help you navigate the complexities that arise when handling large data siloes.
Let’s talk use case
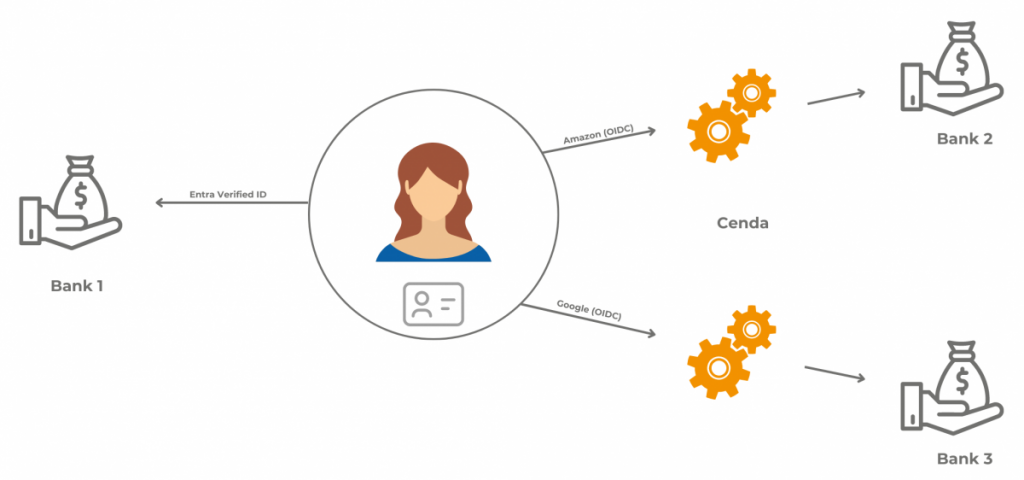
In scenario 1, the user would like to get a loan from Bank 1. In order to do this, Bank 1 must verify the users digital identity via their bank account with Bank 2 and their mortgage account with Bank 3. The identity credential issued by both Bank 2 and Bank 3 are on different services providers.
Cenda is able to integrate within the other decentralised providers to ensure Bank 1 can successfully verify the credential.
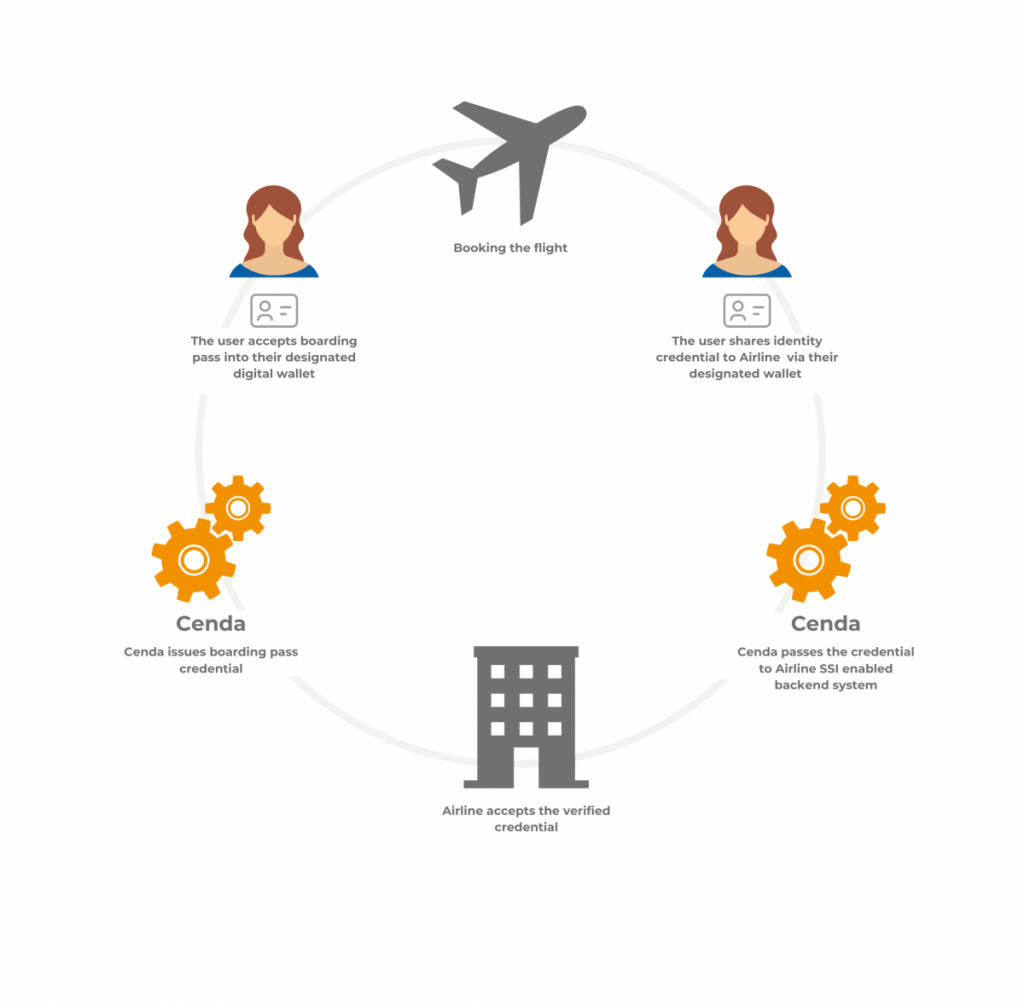
Scenario 2, the user is booking a flight and needs to share their digital identity to the Airline via their designated digital wallet that is not supported by the Airline.
Cenda is able to integrate within the Airline’s system to cooperate with the designated digital wallet, this could be Web Wallet, MS Authenticator App or WaltID.
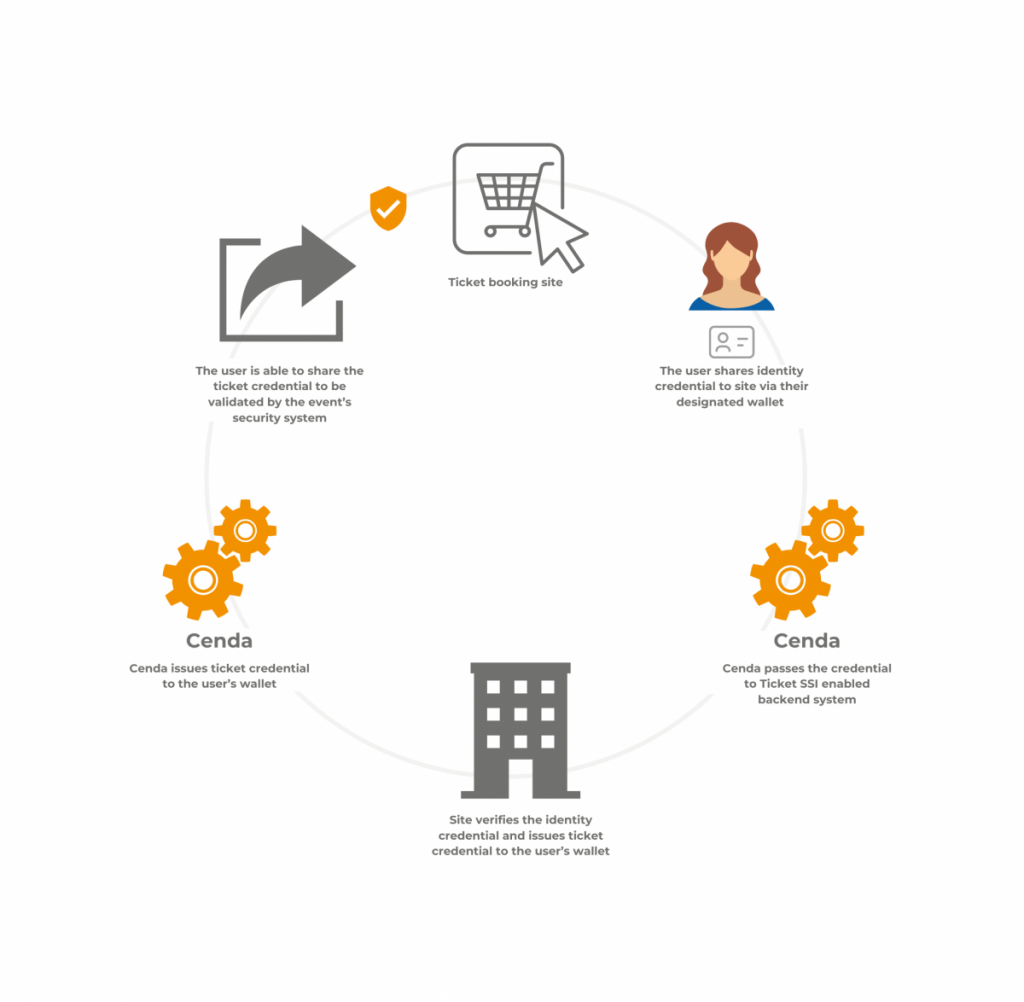
Scenario 3, the user would like to purchase a ticket to a music event, using their digital identity credential, the event owners are able to verify the user is who they say they are and provide them with a ticket credential to access the event.
The event owners have enlisted a third party security organisation for the event.
Cenda has been integrated to create a trust ecosystem between the event organiser and the event security organisation so the authenticity of the ticket credential can be trusted.
Design your use case
If you’d like to understand a specific use case for your industry, share some information with our team, and we’ll explain how Cenda could solve your specific problem.
How we’ll work together
- Sector Analysis
- Stakeholder engagement
- SME Advice
- Use Cases
- Component Evaluation
- POC Scoping
- POC Financials
- POC Delivery
- Production Readiness
By combining these detailed steps with the innovative capabilities of Cenda, we offer a holistic approach to online identity solutions that are tailored to your sector’s unique needs. Our process is designed to ensure that the solutions we develop are not only technologically advanced but also practical, sustainable, and aligned with your strategic objectives.
Current deployments
 Condatis verifiable workplace credentials To continue streamlining the way we operate here at Condatis, we implemented Microsoft Azure AD Verifiable Credentials in our daily work processes. Verifiable credentials help us further secure the way visitors access our office, increase staff onboarding efficiency, and simplify our on-site health and safety procedures. By using verifiable credentials, we can fully trust records… Learn more
Condatis verifiable workplace credentials To continue streamlining the way we operate here at Condatis, we implemented Microsoft Azure AD Verifiable Credentials in our daily work processes. Verifiable credentials help us further secure the way visitors access our office, increase staff onboarding efficiency, and simplify our on-site health and safety procedures. By using verifiable credentials, we can fully trust records… Learn more Optimising staff movement for Sellafield Ltd – a verifiable credentials case study This verifiable credentials case study covers Condatis and Sellafield's work to optimise staff movement with distributed ledger technology to expand Sellafield's employee identity management capabilities. Learn more
Optimising staff movement for Sellafield Ltd – a verifiable credentials case study This verifiable credentials case study covers Condatis and Sellafield's work to optimise staff movement with distributed ledger technology to expand Sellafield's employee identity management capabilities. Learn more Enhancing student experiences with Microsoft Entra Verified ID Condatis and Microsoft engaged in a Proof of Value project with the Royal Melbourne Institute of Technology. The Proof of Value (PoV) focused on using Azure AD Verifiable Credentials to facilitate smoother student onboarding and use cases to enhance the student experience. Learn more
Enhancing student experiences with Microsoft Entra Verified ID Condatis and Microsoft engaged in a Proof of Value project with the Royal Melbourne Institute of Technology. The Proof of Value (PoV) focused on using Azure AD Verifiable Credentials to facilitate smoother student onboarding and use cases to enhance the student experience. Learn more Rapid frontline staff deployment with the NHS Digital Staff Passport The DSP is built on decentralized technology and enables healthcare workers to control how their identity details are used and stored. With the DSP, a healthcare professional's data is held cryptographically on their mobile device using Connect.Me, Evernym's digital wallet. Learn more
Rapid frontline staff deployment with the NHS Digital Staff Passport The DSP is built on decentralized technology and enables healthcare workers to control how their identity details are used and stored. With the DSP, a healthcare professional's data is held cryptographically on their mobile device using Connect.Me, Evernym's digital wallet. Learn moreWould you like to stay up to date with our Cenda advancements?
Thank you for your interest in our work! Please leave your name, company, and email address below to stay up to date on Cenda.