In previous blog posts, we have covered various topics around identity, the evolution of identity, federated identity, and an extensive introduction to SSI with example uses cases. This blog generalises all defence solutions related to authentication methods of the past and the future while introducing the concept of Identity in Depth.
Note: We would like to thank Professor Bill Buchanan and Basil Manousos at Edinburgh Napier University for letting us use their slides.
Defence in depth
The concepts of Defence in Depth are well known and well applied in IT security settings. The slide below shows Defence in Depth, a concept borrowed by the military and applied to IT Security for the last few decades. The idea is that as an attacker progresses with their attack on IT systems, they should be encountering layers of defence that are becoming harder to crack.
In the real world, the following tools are used at various layers:
- No defence: for publicly accessible information like a company’s website
- Firewalls: segregates the internal network with the outside world
- Internal network zones: enhanced firewalling so that parts of the internal network offer additional access controls (e.g. only allow access from certain workstations)
- IDS/IPS/ Monitoring: systems that monitor for or even prevent attacks
- Endpoint security: includes antivirus, Data Loss Prevention (DLP), etc. for employee computers
- Credentials: usernames and passwords to access various defence layers (e.g. to login to a workstation)
- Physical security: card access and security guards to ensure physical space security
The layers, especially the firewall, the credentials and the physical security, were known as the “perimeter” and so we had the term “perimeter security.” However, the move to the cloud has shifted the perimeter to, well, the cloud. You could almost claim that there is no perimeter at all. All cloud services need to be accessible from anywhere in the world. This makes it harder to use firewalls as a defence, removing a valuable tool from the CISO’s toolkit.
Insiders
Credentials have been used more widely to compensate for losing firewalls as the first line of defence; for example employees are required to VPN into a company machine before they can use cloud-based services. This helps re-introduce the firewall, as the VPN services can now assign the employees an IP. However, the VPN solution introduces a different problem, illustrated below.

The slide above shows three castles which have something in common: they were all conquered with the help of an insider, who opened a back-door to the attackers. In the modern world, the insider could be:
- Credentials stolen from a victim of social engineering
- Credentials stolen via an unrelated third-party service that got compromised, into which an employee had reused their company credentials
- A disgruntled employee or industrial spy
This problem is amplified with the use of cloud and VPN to access it. The attacker now has a way to bypass multiple defences; if they can use a compromised VPN account, they are inside the defence walls.
Identity in depth
Using the full extent of modern Identity solutions can clearly help with stolen credentials. We call this concept Identity in Depth, to designate that it is similar to Defence in Depth but operates on Identity and authentication. This helps enhance not only the VPN access, by enhancing the authentication to it, but any other credential-based service. Here are the authentication solutions forming the current toolbox to practice Identity in Depth.
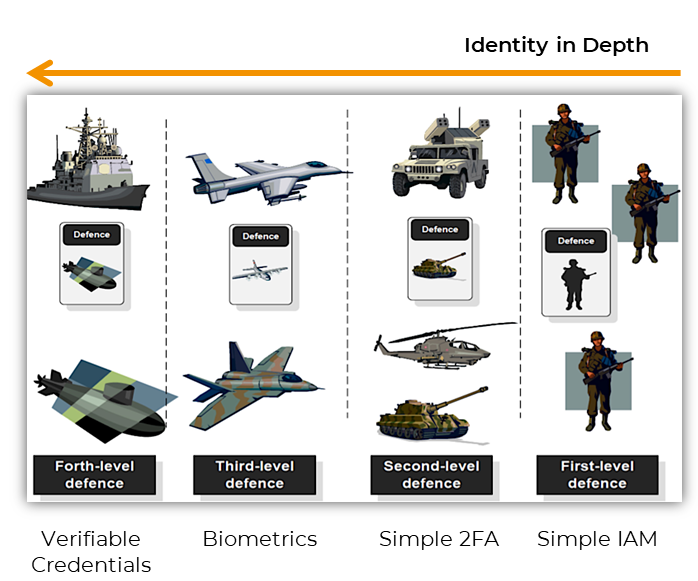
As we see, in this concept, we can have the following layers:
- Simple Identity & Access Management (IAM) solutions typically consist of centrally managed username/password credentials. On its own, it can still be defeated by stolen credentials as discussed earlier
- 2FA: when IAM uses a separate channel to verify the user, then it practices 2FA
- Biometrics: when IAM uses biometric authentication to confirm the user
- Verifiable Credentials: when the IAM solution uses Verifiable Credentials, it introduces the factor of possession (of the credential on the employee’s device)
Conclusion
When we talk modern IAM, and indeed Identity in Depth, the tools remaining at our disposal really are the factors of authentication utilised by the greater IAM solution deployed. As an organisation implements more and more defences, they introduce new factors of authentication, and they improve their Identity in Depth. Verifiable Credentials is the deepest current layer; Not only does it introduce the possession factor, but it also does so in a very easy to use manner. We consider SSI and Verifiable Credentials the most appropriate solution for organisations looking for the most secure IAM that doesn’t hinder usability.