Six key components that contribute to a robust solution.
 Our Business Development Executive, Fiona Edmond, recently hosted a webinar with Technical Lead Dave Downs. In 40 minutes, Fiona and Dave revealed how organisations could optimise customer experience using Microsoft Entra External Identity, specifically Azure Active Directory B2C.
Our Business Development Executive, Fiona Edmond, recently hosted a webinar with Technical Lead Dave Downs. In 40 minutes, Fiona and Dave revealed how organisations could optimise customer experience using Microsoft Entra External Identity, specifically Azure Active Directory B2C.
This session covered what our team believe are the six key components that contribute to a robust solution:
- Knowing your customer
- Federation
- Governance and building your trust framework
- Identity protection
- Data
- Modern security standardisation
In the first edition of this three-part blog series, we’ll cover the first two components discussed during the webinar. As specialists in Azure AD B2C (now part of the Microsoft Entra family) and Verified ID, we want to demonstrate how Azure AD B2C can solve some of the common identity challenges we see businesses face daily.
1. Knowing your customer
Let’s kick things off with the first key area we look at when designing Identity and Access Management (IAM) solutions – Knowing your customer. Consider who uses your digital services, their current demands, and where there is room for future service expansion. Knowing your customer is about who your customers are and what they need to interact with to achieve their objective digitally; this intelligence helps drive what the solutions we build need to do.
Start with considering the type of users you have. Are they internal users? Are they federated to your company’s internal directory, for example, Azure Active Directory, or are they external users? Do they sign in directly using email and password credentials or a social login like Google and Facebook?
Additionally, it would help if you considered whether the solution you need falls into one of these two areas:
- A Business to Customer (B2C) solution is primarily for individual customers, partners and suppliers.
- A Business to Business (B2B) solution is for provisioning external organisations or departments containing individuals with access to your system.
Now that you know who your users are, how does that understanding translate to your Identity and Access Management (IAM) solution?
Azure AD B2C supports credentials used for external users, which can be stored in their directory or externally and accessible through an API.
Azure AD B2C supports federation and is primarily used for internal users or sometimes external users with their own identity store or social login. Generally speaking, Azure AD connects with anything that supports OpenID Connect, OAuth 2, or SAML2.
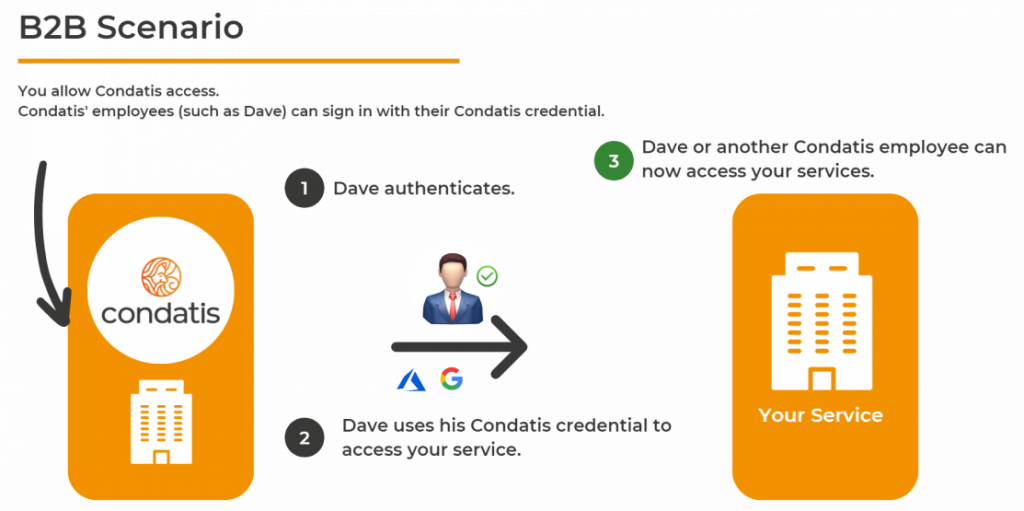 Using an external identity is beneficial as it allows users to reuse an existing identity that they already have. Below we provide two scenarios to help you differentiate between the Azure Active Directory platforms.
Using an external identity is beneficial as it allows users to reuse an existing identity that they already have. Below we provide two scenarios to help you differentiate between the Azure Active Directory platforms.In a B2B scenario, you want to provide Condatis and our employee Dave access to your system. In that case, it’s beneficial for him to use our organisation’s identity as he is likely already signed into it. Here you would most likely be using Azure Active Directory.
In a B2C scenario, you want to provide Dave, as an individual, access to your system, for example, to log in and buy your services. In that case, you may want him to have his own credentials specific to you or allow him to use his personal social ID, like his Google account. Here you would most likely be using Azure AD B2C.
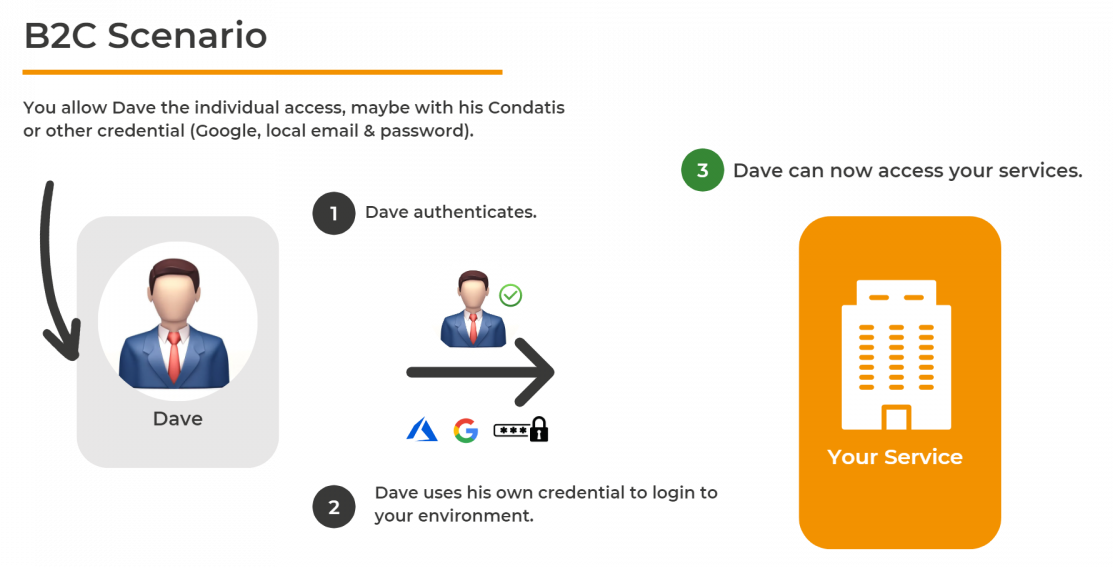 Regarding the split between B2C and B2B, Microsoft Azure Active Directory typically focuses on what’s in the name, Business-to-Customer (B2C) or Business-to-Business (B2B). What you’ll need depends on your use case, and you might have a mixture of the two, for example, if you want to provide access to individual customers but also onboard organisations or allow members of your own organisation to administer the system.
Regarding the split between B2C and B2B, Microsoft Azure Active Directory typically focuses on what’s in the name, Business-to-Customer (B2C) or Business-to-Business (B2B). What you’ll need depends on your use case, and you might have a mixture of the two, for example, if you want to provide access to individual customers but also onboard organisations or allow members of your own organisation to administer the system.
2. Federation
Now, let’s look at our second key component, federation. We’ll explore what it is and what it means for customers. The best way to think about federation is that some existing identity is stored outside B2C; this might be Azure Active Directory, a social identity provider such as Google, Twitter, and Facebook, or some other standards-compliant identity provider.
With this information, a link between B2C and the identity provider should be registered. This link allows B2C to redirect the user to the identity provider to authenticate and for the identity provider to return a response back to B2C.
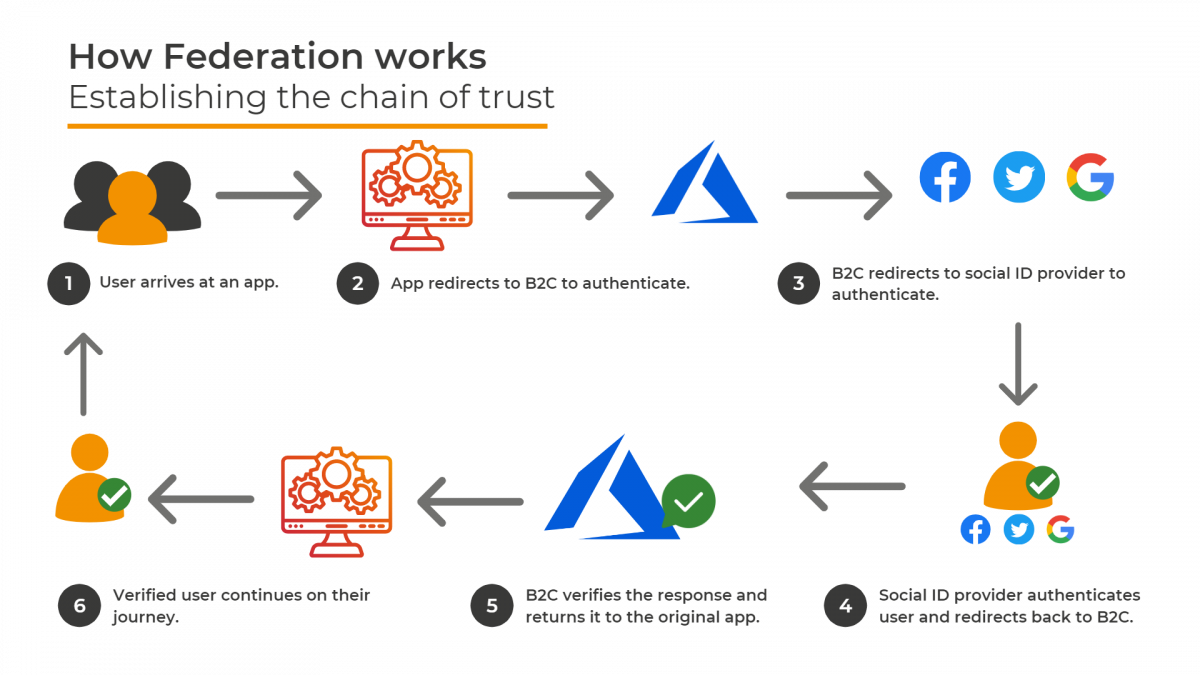
With this journey in mind, while B2C is ultimately responsible for authenticating the user from the application’s point of view, the application trusts B2C to handle that authentication using whatever process B2C deems necessary.
B2C then trusts the Identity Provider (IdP) to actually perform the authentication. If the IdP returns a signed-in user to B2C, then B2C can return the signed-in user to the application. This establishes a chain of trust – as the app trusts B2C and B2C trusts the identity provider. From a user’s point of view, it allows them to reuse their existing identities securely. This means there is no need to set up new accounts.
Stay tuned for the next instalment of this series, where we’ll cover the following four key components for a complete Azure AD B2C solution. Check out the webinar in full on our YouTube channel. To dive deeper into Azure AD B2C, catch up on our complete series on ‘Getting Started with Azure AD B2C’.
Get more content like this straight to your inbox!
Subscribe to stay up to date.