Decentralized identity, what was once a concept, is a technology continuing to grow into a vital part of today’s digital world. The concept that once looked to put the user in control of their data, is now very much real, and being developed further by our experts in the field. In this article, Solutions Architect, Richard Astley takes it back a few steps, and helps you understand decentralized identity; Richard talks about the importance of identity, the links between physical and digital wallets, verifiable credentials, and more.
How wallets turned digital
 What is my identity? How do I use it? And more importantly, how could I be using it?
What is my identity? How do I use it? And more importantly, how could I be using it?I will first look at something I carry everywhere with me, it’s very personal to me, I am sure you have one too. I carry mine in my back pocket and I feel totally lost if I don’t have it with me. Can you guess what it is?
Yes, My Wallet.
So, what do I keep in my wallet?
I keep my bank and credit cards, which are used to withdraw cash from my bank account or to pay for things in person or online. Unfortunately, in the past they have also let someone else make purchases online too. I have my driver’s license which I use to prove my entitlement to drive or sometimes my address or date of birth. I have my emergency breakdown cover card just in case I need a bit of help while travelling, as well as my gym membership which I use to access the gym, I say gym, but I really mean the sauna.
I also have lots of loyalty cards which, it seems, every other company is now giving out to try to retain me as a customer, and offer some sort of incentive for my repeat business. I have so many of these that I have started refusing any new cards as my wallet can only hold so much., I always feel I might be missing out, but I would need to carry a suitcase instead of a wallet if I wanted to take them all. Finally, I also have lots of receipts that I am sure were important at some point but now just act as a sort of booster cushion and get cleared out a few times a year.
I always carry all this information around with me. These cards form part of my identity and let others provide a service when I present them because they trust the companies, departments or organizations that have issued them to me. I don’t carry all my identity in my wallet, I have some parts like my work id, my passport or some utility bills that only come with me for work or on special occasions, if I need to travel to other countries or if I need to supplement other parts of my identity.
Now let’s look more in depth from a digital standpoint
As well as carrying my wallet with me I also carry my mobile phone, which I use for making small payments with, instead of my bank card. It’s so easy, I can just pay by using my thumb print instead of my pin number and I know it’s only me who can use it.
My wallet is great for using in the physical world, where I can just show someone my cards with my identity credentials but how do I use my identity in the digital world?
In the digital world most of us already have some form of digital identity that we use. We rely on lots of different identity providers that we build relationships with like Google, Facebook, or other federated identity providers like the Microsoft accounts we use for work. We login to digital services using these identity providers to share our identity.
So, when we use our digital identity, we are really talking about interacting with a digital service, which are sometimes called relying parties. A relying party relies or depends on our digital identity information to provide their services to us. For a relying party to provide their service the relying party must have a trust relationship with one of our identity providers and trusts that the identity provider has authenticated us securely and that they are asserting accurate and up to date information about us.
The identity provider must also trust the relying party to treat the returned data securely and to trust it only for the time defined by the identity provider.
When we interact with a relying party, they tell us the identity providers they have a trust relationship with and we can authorise our trusted identity providers to assert our information to the relying party and because the relying party trusts the identity provider is asserting the correct information, they can agree to provide their service.
So, in a centralised world we give permission for identity providers to share our information with a relying party which works well for certain information like our name, email addresses, our employment details or for authentication purposes, but it can’t really work for all credentials that have been issued in the real world or all relying parties that require access to the same credentials.
A new approach to identity, a Decentralized Identity.
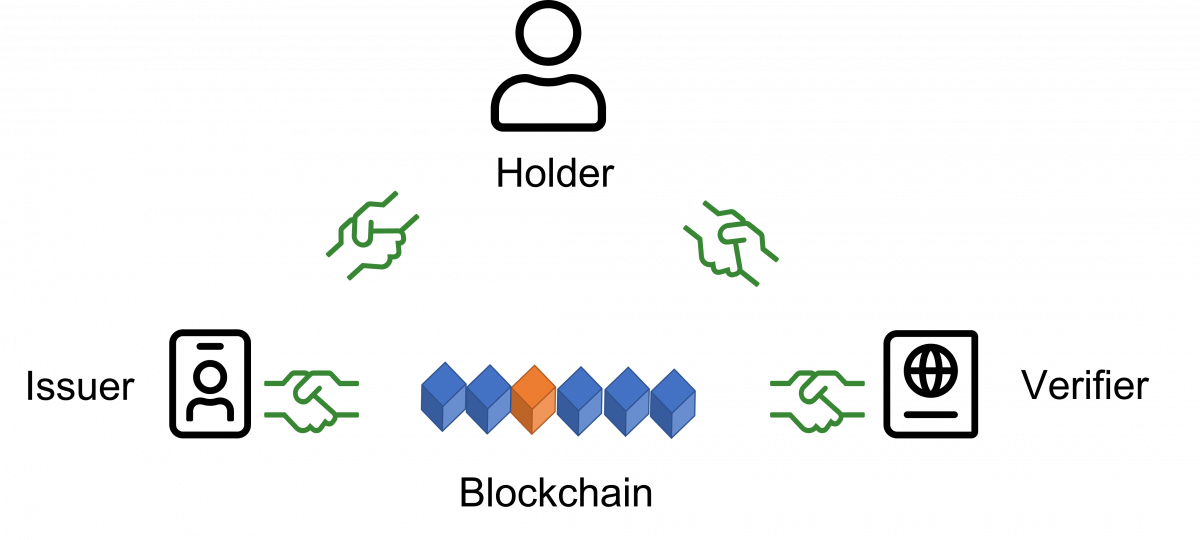 What if we had a digital wallet that we can keep on our phones that would allow us to share a digital version of our physical credentials in a manner that is more secure and tamper evident than their physical counterparts, ensuring that the information being submitted to a relying party has come from a trusted source and has been shared from the wallet they were issued to?
What if we had a digital wallet that we can keep on our phones that would allow us to share a digital version of our physical credentials in a manner that is more secure and tamper evident than their physical counterparts, ensuring that the information being submitted to a relying party has come from a trusted source and has been shared from the wallet they were issued to?
This is where Decentralized Identity comes in, Decentralized Identity allows people and organisations to manage and control their own digital credentials.
Using Decentralized Identity still allows identity providers to issue information about me but instead of sharing this information with a relying party directly, they give me the credential and anytime I interact with a relying party I share this credential directly.
This new identity model is still based on trust.
The identity provider must be trusted to assert accurate data about me, but we no longer call them an identity provider, we call them an issuer and they issue credentials about a subject to a holder, the person with the digital wallet.
I still must trust that the relying party is only going to use my data for the intended purpose. A relying party now verifies credentials in Decentralized Identity, so we call them a verifier. The verifier still must trust the issuer who issued the credential and have a way to check that what the holder shared with the verifier is the credential the issuer issued.
How does this all work?
Underpinning it all are two new standards that support decentralized identity, both standards are held by the world wide web consortium W3C.
These standards are Verifiable Credentials Data Model (W3C) and Decentralized identifiers (W3C)
A verifiable credential is a data model used for encoding, signing, exchanging, and verifying digital credentials. This means a verifiable credential is a piece of information about a user that is cryptographically signed by the organisation issuing it, such as a bank, university, or employer, and stored in the user’s digital wallet. When an issuer makes assertions about a subject they are issued as verifiable credentials.
Decentralized Identifiers or DIDs are globally resolvable identifiers, a bit like domain names but instead of resolving to an IP address, they resolved to a did document instead.
There are many different ledgers used to store DID documents so did identifiers are made up of three parts “did:ion:4564sd65f465s4”, the first part being the schema “did” which tells us it identifies a DID document, the second part is the Method like “ion” which identifies the ledger needed to resolve the DID document and the third part is the Method-Specific Identifier used to locate the DID document within that ledger.
To prove that a credential has been issued by a trusted organisation and not tampered with, the credential issuer creates a DID document describing their verification method which also contains their public key and writes it to a blockchain distributed ledger. Using this form of public key exchange DIDs allow you to identify and share public keys between issuers, holders, and verifiers and makes decentralized identity possible by creating this trust between parties using DIDs and public keys rather than requiring federated relationship to provide trust in a centralized identity system.
Using these standards allow an issuer to issue a verifiable credential that is signed with their private key to a holder to store in their digital wallet.
If asked by a verifier to share their information, the holder can share the verifiable credential with the verifier. The verifier can resolve the issuers public key needed to verify the credential and check it was signed by the issuer, this ensures the credential was issued by the issuer and has not been tampered with. Verifiers can trust whichever issuers they want allowing them to build their own governance with trust frameworks of who they trust and what information they trust them to provide.
So, what does Decentralized Identity allow us to do?
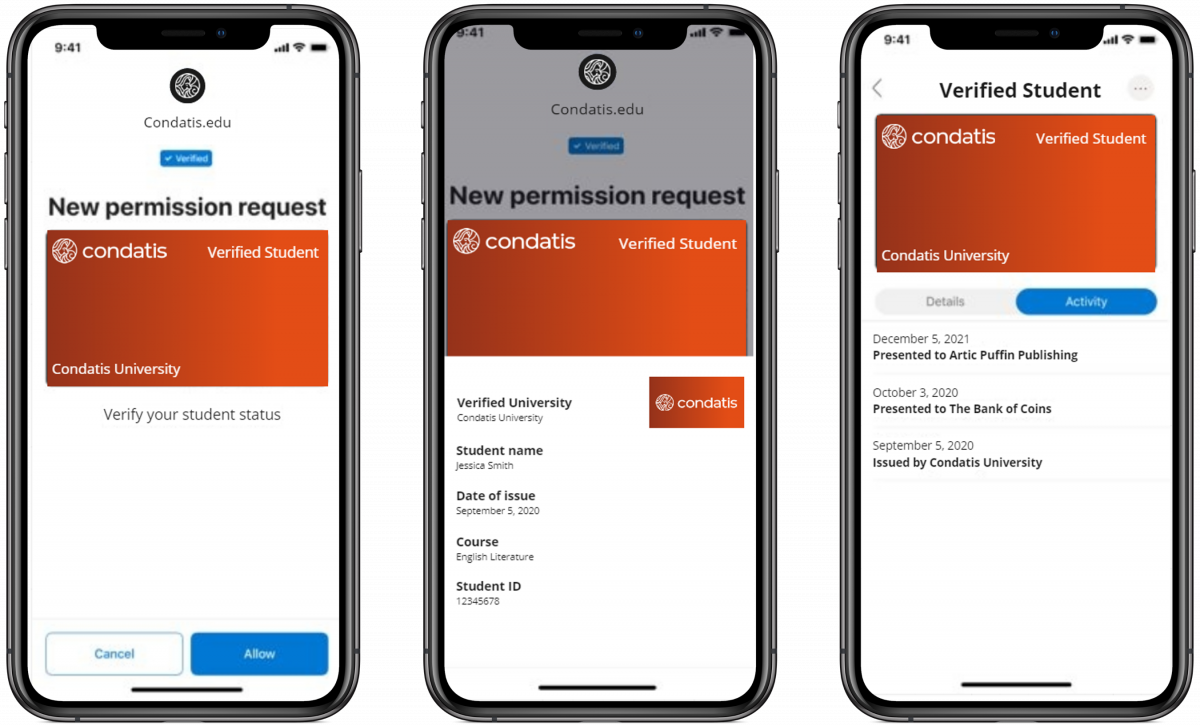
Decentralized Identity allows us to have more control over our digital identity by allowing us to hold and manage our own identity credentials, choosing who we share them with and for what purpose. It allows Governments, Education Institutions, Health providers, Organizations, Companies, and workplaces to issue digital versions of the credentials they issue in the physical world and allowing us to prove our identity credentials online with the same if not more trust than the credentials in their physical form.
We will be able to sign up for new digital services using our trusted identities, removing opportunities for identity theft. Services can be sure we are who we say we are allowing new self-service opportunities while still providing the same level of assurance that would have previously needed physical identity checks. We can be granted access to resources securely using our identity which is only in our control.
Governments could issue identity credentials that could be used across all their services at local and national levels, you could fill in a tax return with the same credential used to access a local library or even reuse this trusted credential in the private sector as a highly trusted identity credential extending the reach of your government identity beyond its federated boundaries.
Driver’s licenses can become digital allowing you to prove your entitlement to drive online reducing the need for face-to-face verification when renting vehicles, with the assurance provided with Verifiable Credentials photocopies of identity documents as proof of checks can become a thing of the past.
Employees could safely move between sites proving their identity, qualifications, and experience needed to carry out their role. Doctors and nurses can move freely between hospitals, streamlining the onboarding processes with quick highly assured verifications that meet any governance checks needed to safe-guard hospitals or any other secure site.
Employers could verify qualifications digitally when applying for a new job or even issue their own training records for you to carry on to your next job.
Retail and Hospitality companies can issue as many loyalty cards as they want, and we can unlock all the rewards. Gyms can issue memberships credentials and we can leave our wallets or purses at home when we go to the gym.
Conclusion
As more of our interactions become digital, decentralized identity provides everyone using the web with a new way to trust each other. Trust does not require managements of relationships with client IDs, secrets and API integrations with every possible identity provider, attribute provider or relying party, but instead allows each of us in isolation to build our own trust and verify any credential without having any previous relationship with the issuer. Decentralized Identity is not a replacement for our centralized identity, but instead just a new way of carrying and sharing our identity beyond federated limitations with unlimited reuse with any party we choose.
1 comment
Comments are closed.